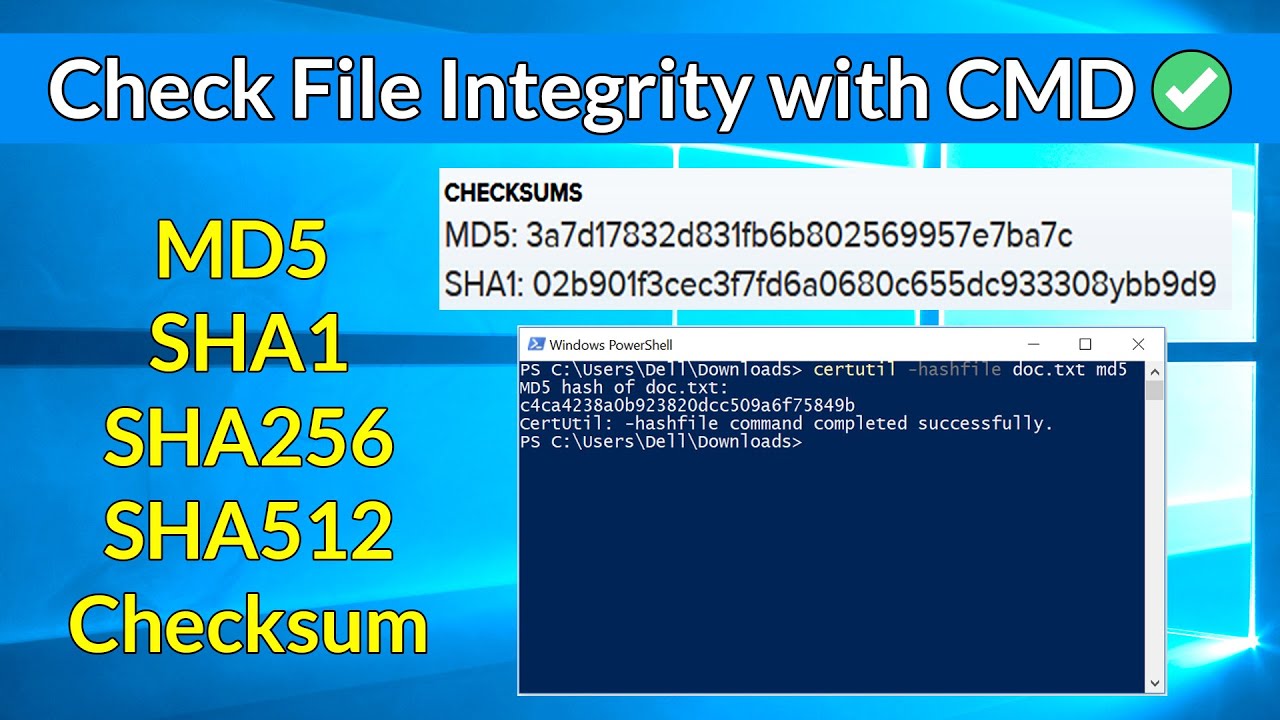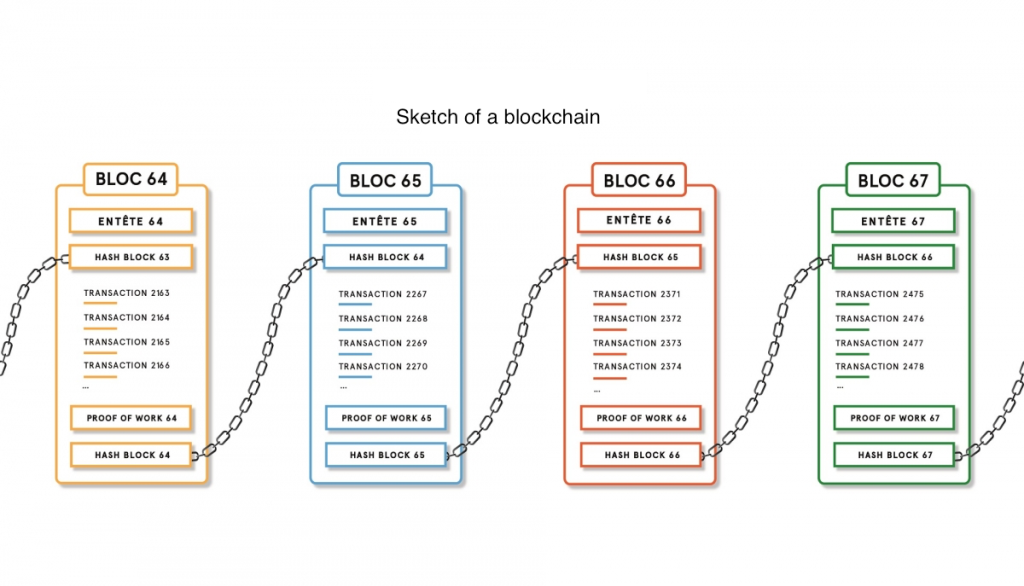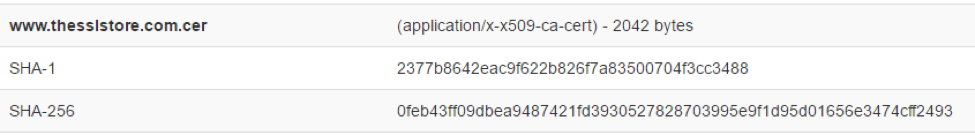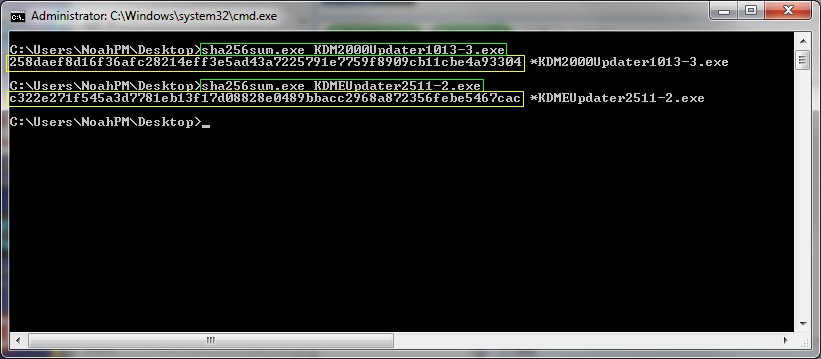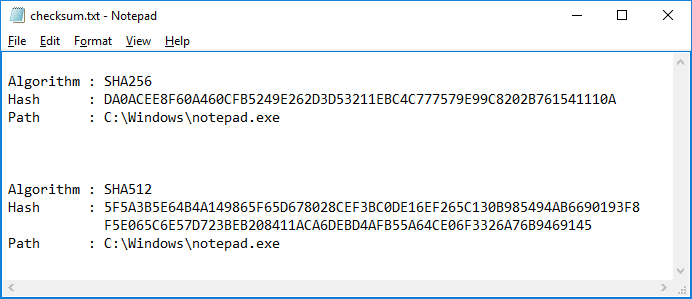
How do you determine the SHA-256 or SHA-512 checksum of a file? - ID: 109483101 - Industry Support Siemens
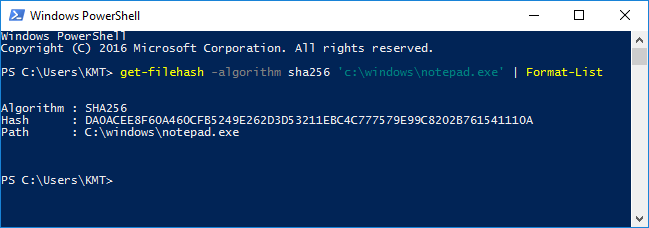
How do you determine the SHA-256 or SHA-512 checksum of a file? - ID: 109483101 - Industry Support Siemens
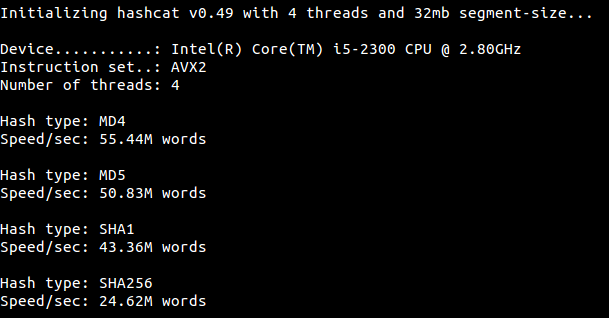
![Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots] | EduStorage.net Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots] | EduStorage.net](https://www.edustorage.net/files/hashcat/cracked-sha256-pass.png?d00c4396d8)
Is it possible to crack a password hashed with sha256 with hashcat? [with screenshots] | EduStorage.net